The GIAC Reverse Engineering Malware (GREM) certification is a top credential for cleared professionals focused on combating advanced cyber threats. It validates essential malware analysis skills like reverse engineering, memory forensics, and bypassing obfuscation – key abilities for safeguarding government and defense networks. With average salaries of $124,000 and rising demand for cybersecurity experts, GREM certification can significantly enhance your career prospects in roles like Malware Analyst, Cyber Threat Intelligence Expert, and Incident Responder.
Key Takeaways:
- Who It’s For: Cybersecurity professionals with TS/SCI clearance aiming to specialize in malware analysis.
- Skills Validated: x86/x64 assembly, memory forensics, unpacking executables, analyzing malicious documents, and more.
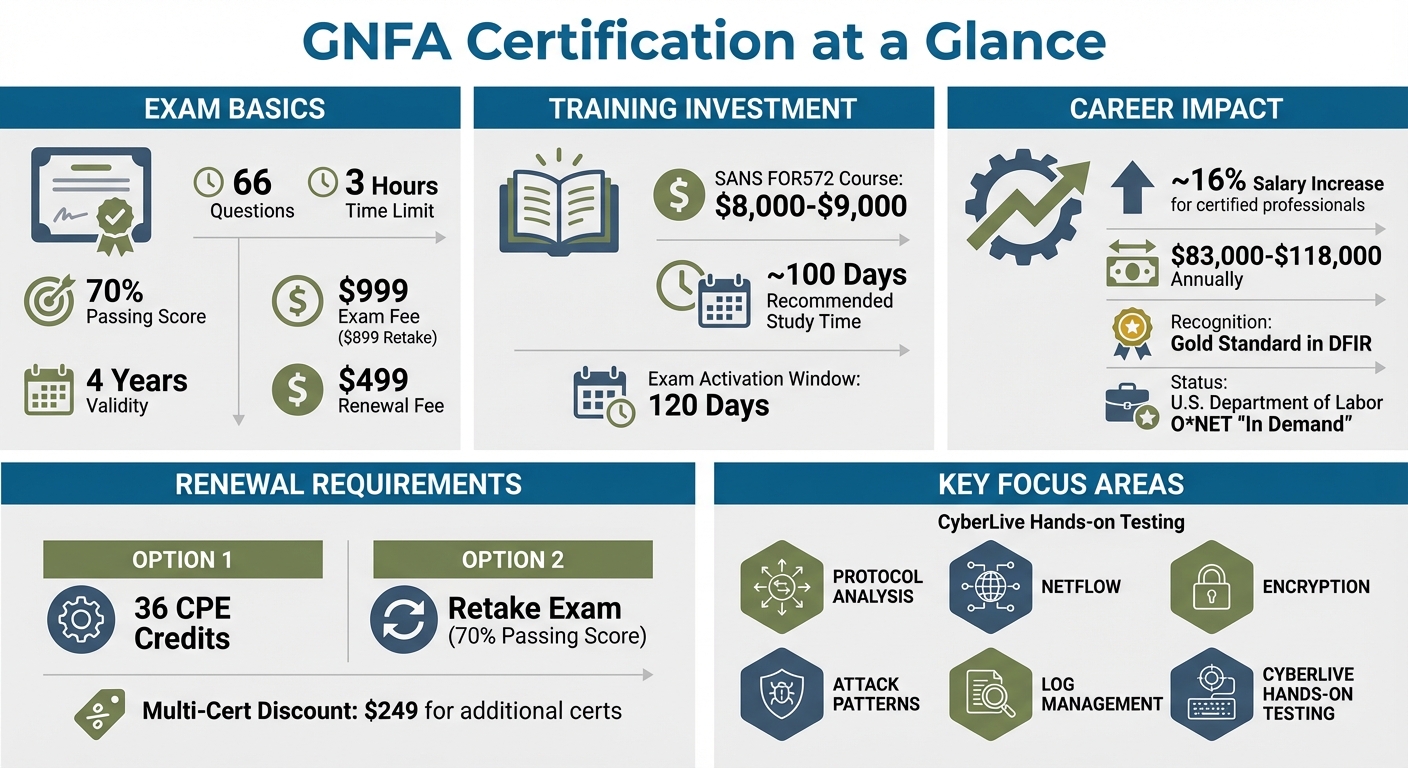
- Exam Details: 66 questions, 3-hour limit, 73% passing score, $1,299 fee.
- Preparation: SANS FOR610 course (~$8,600), hands-on labs, and practice exams.
- Career Benefits: High-paying roles in government, defense, and intelligence sectors with salaries up to $260,000.
The GREM certification not only sharpens your technical skills but also positions you as a sought-after expert in the growing field of cleared cybersecurity.
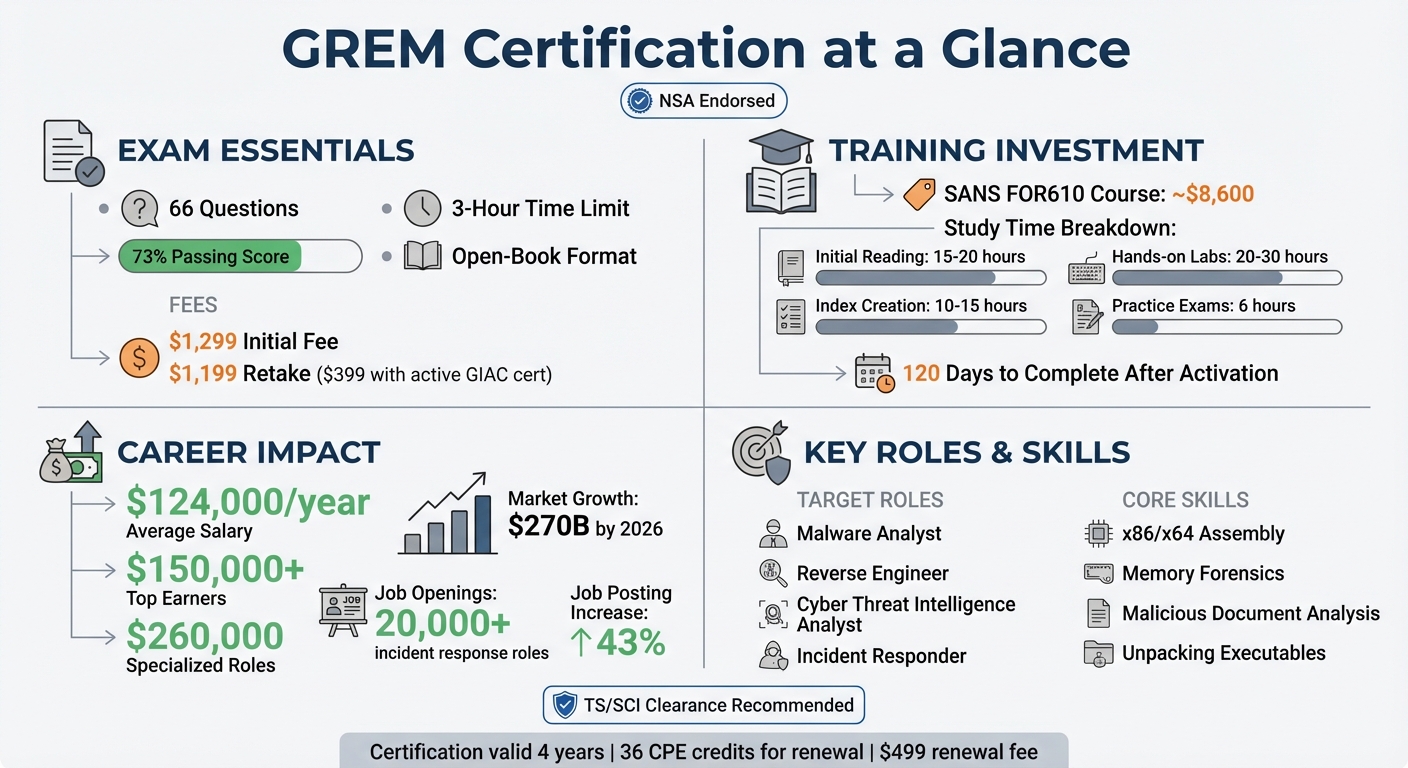
GREM Certification Quick Reference Guide: Exam Details, Costs, and Career Benefits
GREM Certificate Review (Reverse engineering malware)
What the GREM Certification Covers
The GREM certification is designed to validate advanced reverse engineering skills, focusing on your ability to analyze and deconstruct sophisticated malware.
Core Skills Validated by GREM
The certification tests your expertise across key areas of malware analysis. You’ll need to demonstrate skills in static analysis (like examining file headers and strings) and dynamic analysis (using debuggers to follow code execution). A significant portion of the exam focuses on x86/x64 assembly language, where you’ll analyze instruction patterns, reverse functions to understand parameters and return values, and interpret execution flow controls such as loops and conditional statements.
Another critical area is the analysis of malicious documents. This includes tasks like dissecting macros in Microsoft Office files, analyzing suspicious PDFs for embedded JavaScript, and extracting shellcode from RTF files. You’re also expected to show proficiency in unpacking protected executables, repairing Import Address Tables (IATs), and deobfuscating malicious JavaScript used in web-based attacks. Advanced skills include conducting memory forensics using tools like Volatility and overcoming anti-analysis techniques such as debugger detection and execution flow misdirection.
"GREM-certified technologists possess the knowledge and skills to reverse-engineer malicious software (malware) that targets common platforms, such as Microsoft Windows and web browsers." – O*NET
The certification also emphasizes the use of industry-standard tools like Ghidra, IDA Pro, x64dbg, Wireshark, and PEview. These tools are central to the exam’s CyberLive component, a hands-on virtual lab where you solve practical tasks using real programs, code, and virtual machines. This practical element underscores the certification’s focus on preparing professionals for real-world challenges.
Exam Format and Certification Requirements
The GREM exam evaluates your ability to apply these technical skills in realistic scenarios. It consists of 66 questions, completed within a 3-hour time limit, with a passing score of 73%. The exam is open-book, allowing candidates to bring hard-copy reference materials and personal indexes. Many successful test-takers create detailed, alphabetized indexes covering tools, command-line switches, and assembly patterns to streamline their exam process.
The initial exam fee is $1,299, which includes two practice tests. Retakes cost $1,199, or $399 if you hold an active GIAC certification. Once earned, the certification remains valid for four years. To maintain it, you’ll need to earn 36 Continuing Professional Education (CPE) credits or retake the current exam. Renewal costs $499.
How to Prepare for the GREM Certification Exam
Training with the SANS FOR610 Course
The SANS FOR610: Reverse-Engineering Malware course is considered the go-to preparation for the GREM certification. At around $8,600, the six-day course builds skills progressively. Here’s a quick breakdown of what to expect:
- Day 1: Fundamentals and setting up your lab environment.
- Day 2: x86/x64 assembly and Win32 APIs.
- Day 3: Analyzing malicious documents like PDFs, Office macros, and RTF shellcode.
- Day 4: Tackling obfuscated JavaScript, VBScript, and unpacking malware.
- Day 5: Techniques to bypass anti-debugging and anti-virtual machine defenses.
- Day 6: The Malware Analysis Tournament, a Capture-the-Flag challenge to apply everything you’ve learned.
The course provides a robust lab environment featuring tools like Ghidra (the primary static analysis tool), x64dbg, Scylla, and Sysinternals utilities. To maximize your preparation, supplement the course with targeted practice exams and a custom index for quick reference during the test.
Additional Study Resources and Tools
The GREM exam includes hands-on tasks in the CyberLive format, requiring you to analyze real programs and code. To prepare, take full advantage of the two practice exams provided with the course. These will help you get comfortable with the format and pacing.
One of the most effective strategies for the open-book exam is creating a custom index. Spend 10–15 hours building a detailed index from the five SANS course books. Use color-coding to organize tool names, command-line switches, and page references. This preparation can save you valuable time during the test.
"The open book format sounds great in theory, but you really need those tabs and bookmarks to make it work – otherwise you’re just burning time hunting through pages." – Ethan Marshall [6]
Study Schedules and Time Management
Once you activate your certification attempt, you have 120 days to complete the exam. Here’s how you can structure your study plan:
- Initial Reading: Spend 15–20 hours going through all five course books to familiarize yourself with the material.
- Hands-on Labs: Dedicate 20–30 hours to mastering tools like Ghidra and x64dbg. Repeat the labs until you’re comfortable with the commands.
- Index Creation: Allocate 10–15 hours to build your custom index for quick lookups during the test.
- Practice Exams: Set aside 6 hours to take and review the practice tests.
Here’s a breakdown of the time investment:
| Study Component | Time Investment | Purpose |
|---|---|---|
| Initial Book Reading | 15–20 Hours | Familiarize yourself with key concepts |
| Hands-on Labs | 20–30 Hours | Gain proficiency with tools and techniques |
| Index Creation | 10–15 Hours | Build a quick-reference resource |
| Practice Exams | 6 Hours | Assess readiness and improve pacing |
Pay extra attention to the malicious documents section. Tools for analyzing PDFs, RTFs, and Office macros often have tricky command-line syntaxes that can trip you up [6]. Aim to spend no more than two minutes per question to ensure you have enough time for the more complex CyberLive tasks [2].
sbb-itb-bf7aa6b
Career Benefits of GREM in the Cleared Cybersecurity Field
How GREM Builds Professional Credibility
The GIAC Reverse Engineering Malware (GREM) certification is widely regarded as the benchmark for mastering malware analysis, particularly on platforms like Microsoft Windows and web browsers [2]. Its CyberLive testing component requires hands-on expertise in a virtual lab environment, replicating real-world scenarios [1].
For cybersecurity professionals working in cleared environments, this credential carries extra weight. The United States National Security Agency (NSA) officially endorses GIAC certifications, including GREM, which can significantly boost your reputation when collaborating with government agencies or defense contractors [7]. Because GREM is known for its high level of difficulty and technical depth, earning it signals a strong commitment to skill development – a quality highly valued in the defense and intelligence sectors [2][3].
"GREM acts as a third-party endorsement that tells hiring managers, project leads, or stakeholders, ‘This person knows what they’re doing.’" – PassGuide [3]
This recognition of expertise directly translates into a competitive edge in the job market.
Job Market Advantages for GREM-Certified Analysts
Holding a GREM certification opens doors to specialized roles that demand advanced malware analysis skills. These include positions like Malware Analyst, Reverse Engineer, Cyber Threat Intelligence Analyst, and Incident Responder [2][3]. The certification is officially classified as "in demand" by O*NET and is directly tied to military occupational specialties [2][5].
GREM-certified professionals are well-compensated, with average salaries around $124,000 per year and top earners in niche roles exceeding $150,000 [2][3]. Government agencies and defense contractors often prioritize or even require GREM certification for advanced threat analysis and malware research roles [3]. Additionally, this certification can pave the way to leadership roles such as Senior Malware Analyst, Threat Research Lead, or Director of Threat Intelligence [3].
With the global cybersecurity market expected to reach $270 billion by 2026, the demand for specialists capable of addressing highly sophisticated threats will only grow [2][3]. For professionals in the cleared cybersecurity field, the GREM credential not only positions you at the forefront of this expansion but also underscores your ability to safeguard critical national security interests through advanced technical expertise.
Using GREM Certification on Cleared Job Boards
Building on the career benefits of GREM certification, here’s how to showcase your qualification on job boards and maximize your chances in the cleared cybersecurity field.
How to Highlight GREM Certification on Your Resume
Make your GREM certification stand out on your resume. Feature it prominently in both the "Certifications" and "Skills" sections to grab the attention of hiring managers. On LinkedIn, take it a step further – add "GREM-Certified Malware Specialist" to your professional headline and display the digital badge in the "Licenses & Certifications" section.
Government agencies and defense contractors are often on the lookout for candidates skilled in tools like IDA Pro, x64dbg, Wireshark, PEview, Ghidra, and Volatility. Include these tools in your resume, especially if you gained expertise in them during your GREM training. Highlight specific accomplishments such as analyzing malware families, uncovering zero-day vulnerabilities, or contributing to threat intelligence initiatives. These details show that you can apply your training effectively in practical scenarios.
Finding GREM-Relevant Jobs with Search Filters
When searching on Cleared Cyber Security Jobs, use focused keywords to find roles that align with your GREM expertise. Start with terms like "GREM", "Malware Analysis", and "Reverse Engineering." Job titles to prioritize include Malware Analyst, Reverse Engineer, Cyber Threat Analyst, and Incident Response Analyst.
For more refined results, filter by technical skills such as Assembly (x86/x64), Static Analysis, Dynamic Analysis, and Unpacking. Searching for specific tools like IDA Pro, Ghidra, or Volatility can also help you identify positions that require your level of expertise. Since most cleared malware analysis roles demand a TS/SCI clearance, applying this filter will help you zero in on the right opportunities.
Once your resume is polished and your job search is targeted, prepare to confidently present your skills during interviews.
Presenting GREM Skills in Job Interviews
In technical interviews, underline the practical nature of your GREM certification. Mention the "CyberLive" testing component, which involves hands-on malware analysis tasks, setting you apart from candidates with only theoretical knowledge.
Explain your systematic approach to malware analysis. Start with initial triage, move into static properties analysis, follow up with dynamic analysis using a debugger, and finish with comprehensive reporting. Use examples from SANS FOR610 labs to illustrate how you identified malware intent – whether by bypassing anti-analysis techniques or extracting indicators of compromise to prevent future threats. Be ready to discuss tasks like analyzing obfuscated JavaScript, decoding base64 payloads, and identifying command-and-control (C2) traffic patterns. This level of detail highlights your ability to tackle advanced, state-sponsored malware, a highly sought-after skill in cleared cybersecurity roles.
Conclusion: Advancing Your Cleared Cybersecurity Career with GREM
Earning the GREM certification showcases your expertise in reverse-engineering malware within cleared environments. With an average salary of approximately $124,000 per year – and top earners making over $150,000 – this credential offers a clear financial advantage[2]. But it’s not just about the paycheck. GREM proves your ability to analyze malware that uses anti-analysis techniques, bypass obfuscation, and combat threats aimed at government and defense systems.
What truly sets GREM apart is its focus on hands-on skills. The certification’s CyberLive component requires you to perform real malware analysis on actual code in virtual environments[1]. This practical testing ensures you’re not just learning theory – you’re proving you can handle real-world challenges in critical, high-security settings. Additionally, because GREM aligns with military occupational specialties and is recognized across federal agencies, it’s especially valuable for professionals with TS/SCI clearances[5].
To prepare, start with the SANS FOR610 course ($7,000), which includes 48 labs directly tied to exam objectives[2]. Create a detailed index for the open-book exam, practice with real malware samples, and aim for practice test scores 5–10 points above the 73% pass threshold. After certification, keep it active by earning 36 Continuing Professional Education (CPE) credits every four years[2][5].
GREM certification not only solidifies your technical expertise but also positions you for key roles like Malware Analyst, Reverse Engineer, or Cyber Threat Hunter. With a 43% increase in cybersecurity job postings and over 20,000 incident response analyst openings in the U.S.[4], the demand for your skills is surging. This credential can open doors to roles in the intelligence community, defense contracting, and federal agencies, setting you up for leadership opportunities in protecting critical government and defense operations.
FAQs
What qualifications and experience do I need to earn the GREM certification?
To earn the GIAC Reverse Engineering Malware (GREM) certification, it’s recommended that candidates have at least two years of experience in fields like cybersecurity, malware analysis, or incident response. While having formal education beyond high school can be helpful, practical, hands-on experience in these areas is key.
Certification requires passing a proctored exam that tests both theoretical knowledge and practical skills. Many professionals prepare by enrolling in specialized training, such as the SANS course Reverse-Engineering Malware (FOR610), or by gaining expertise through real-world experience. Familiarity with malware behavior, reverse engineering tools, and analysis techniques can make a big difference in your readiness.
How can the GREM certification help advance a career in government cybersecurity?
The GREM certification is a powerful credential for advancing your career in government cybersecurity. It showcases your expertise in malware reverse engineering – a critical skill for identifying, analyzing, and addressing malicious software that targets systems like Windows and web platforms. These are areas of particular importance for government agencies.
By earning the GREM, you demonstrate practical, hands-on experience that is highly sought after in roles such as forensic investigations, incident response, and system administration. This certification positions you as a strong candidate for advanced positions and leadership roles, especially as the need for skilled malware analysts continues to grow alongside evolving cyber threats. Beyond validating your technical skills, the GREM helps you stand out in a competitive field, paving the way for greater responsibilities and career growth in government cybersecurity.
What are the best resources to prepare for the GREM certification exam?
Preparing for the GREM (GIAC Reverse Engineering Malware) certification exam involves a combination of structured learning and hands-on practice. A standout resource for this is the FOR610: Reverse-Engineering Malware: Malware Analysis Tools and Techniques course. This course dives deep into essential malware analysis methods and tools, making it a valuable starting point.
To supplement your learning, consider books like Practical Malware Analysis, The IDA Pro Book, and Reversing. These are well-regarded in the field and provide detailed insights into reverse engineering and malware analysis.
Hands-on practice is just as important. Study guides and practice exams tailored to the GREM exam can help you get comfortable with the test format and pinpoint areas for improvement. Pairing these resources with regular, practical experience will give you the skills and confidence needed to excel on the exam.